Kinesis Data Stream as Lambda Trigger in AWS CloudFormation
This AWS CloudFormation YAML template demonstrates how a Kinesis Data Stream stream can be implemented as Lambda Trigger in AWS CloudFormation.
Simply deploy the following template via the AWS CloudFormation console. In the designer the template looks like this:
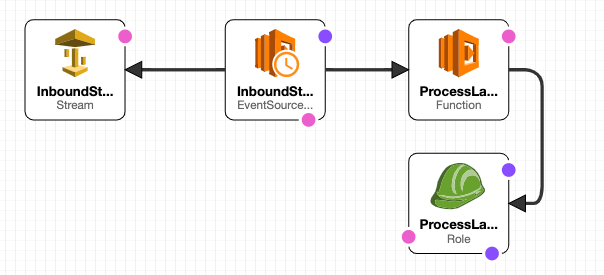
Template:
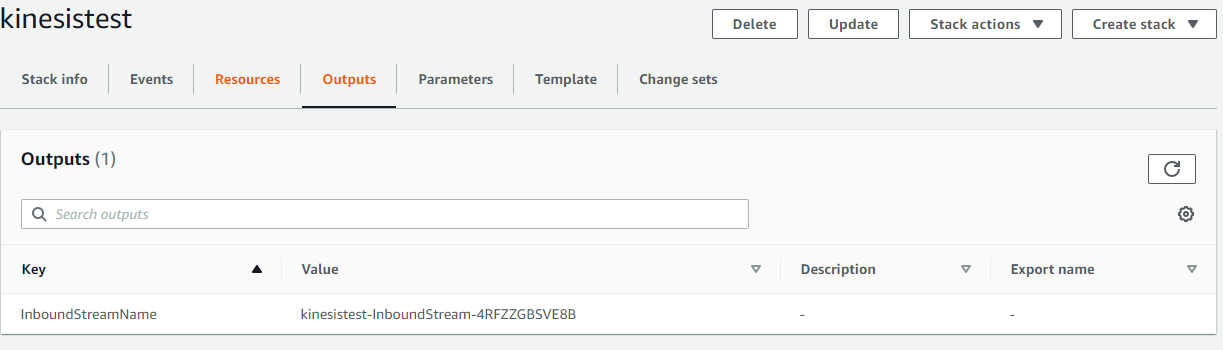
Now we can gather the stream name from the CloudFormation stack outputs section and send a test event using the AWS CLI:
aws kinesis put-record --stream-name <value> --data <value> --partition-key <value>
CLI Reference: https://docs.aws.amazon.com/cli/latest/reference/kinesis/put-record.html
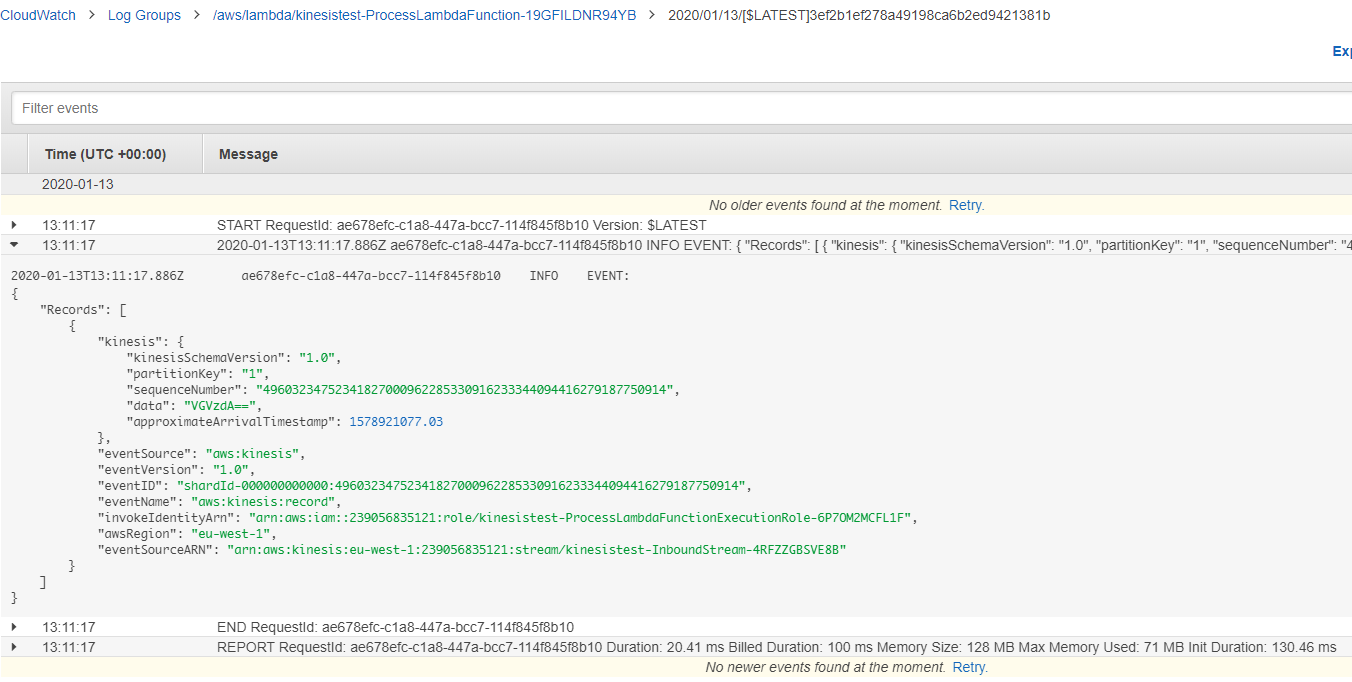
The output should look like this:
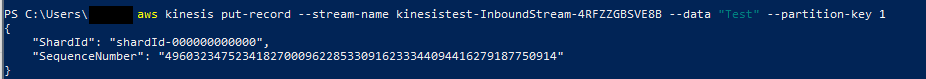
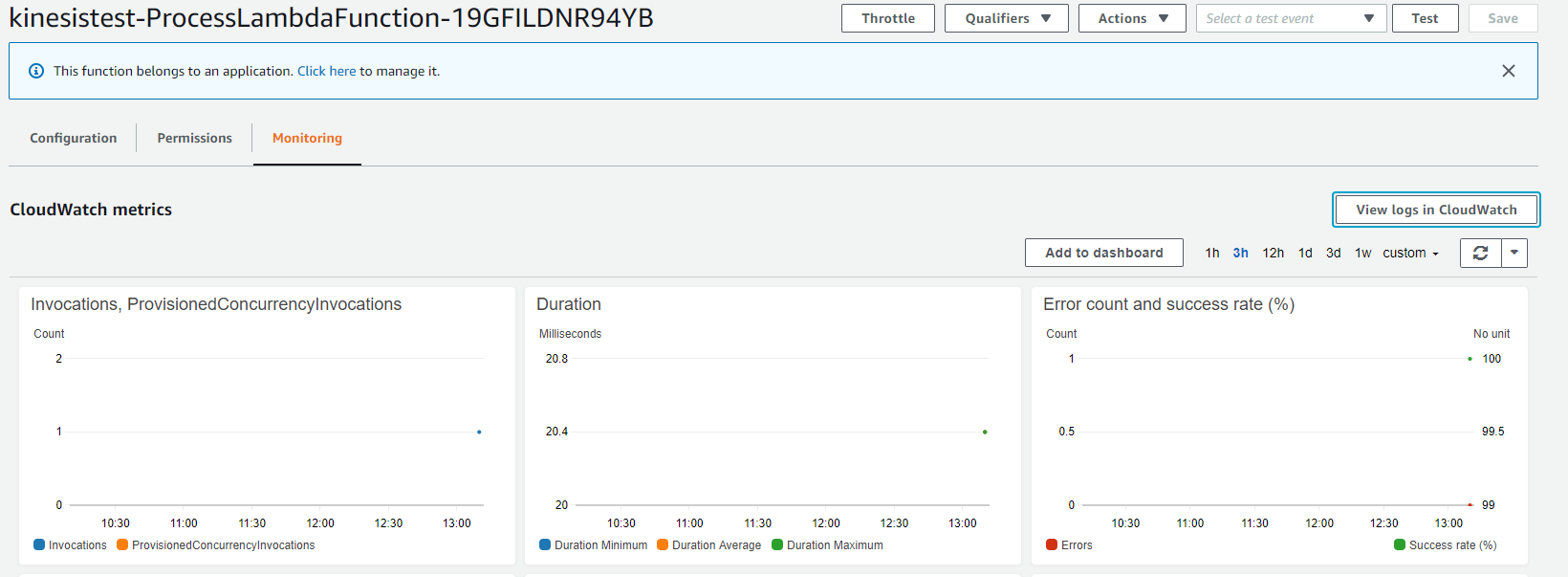
Now you can check in the Lambda Console if the Lambda has been invoked and what has been written to the logs.
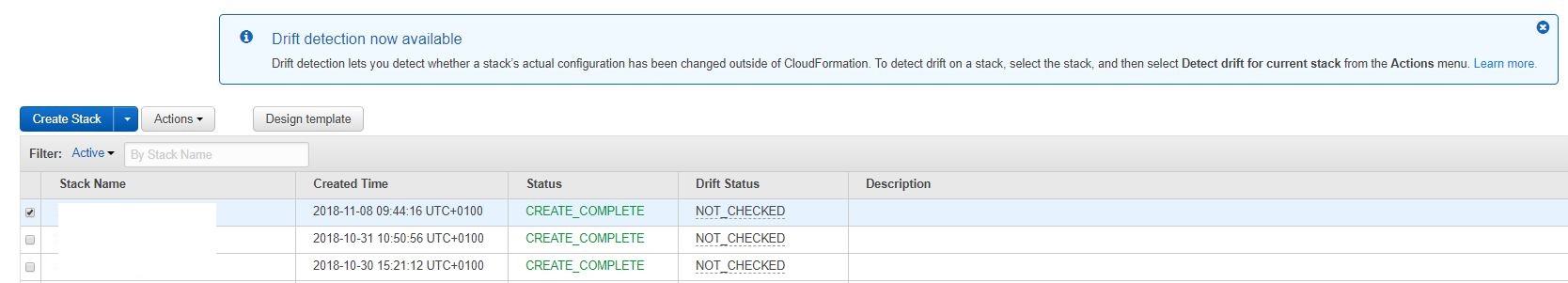 Announced at reinvent 2017 in a CloudFormation Deep Dive session for “early 2018” - now (almost at the end of 2018) the time has come. AWS has added a new and long awaited feature to CloudFormation that will help in many cases: “Drift detection”.
Announced at reinvent 2017 in a CloudFormation Deep Dive session for “early 2018” - now (almost at the end of 2018) the time has come. AWS has added a new and long awaited feature to CloudFormation that will help in many cases: “Drift detection”.