Recently AWS released that the Amazon Simple Queue Service (SQS) is now available as a supported event source for AWS Lambda Functions. You can read the related blog post here:
https://aws.amazon.com/blogs/aws/aws-lambda-adds-amazon-simple-queue-service-to-supported-event-sources/
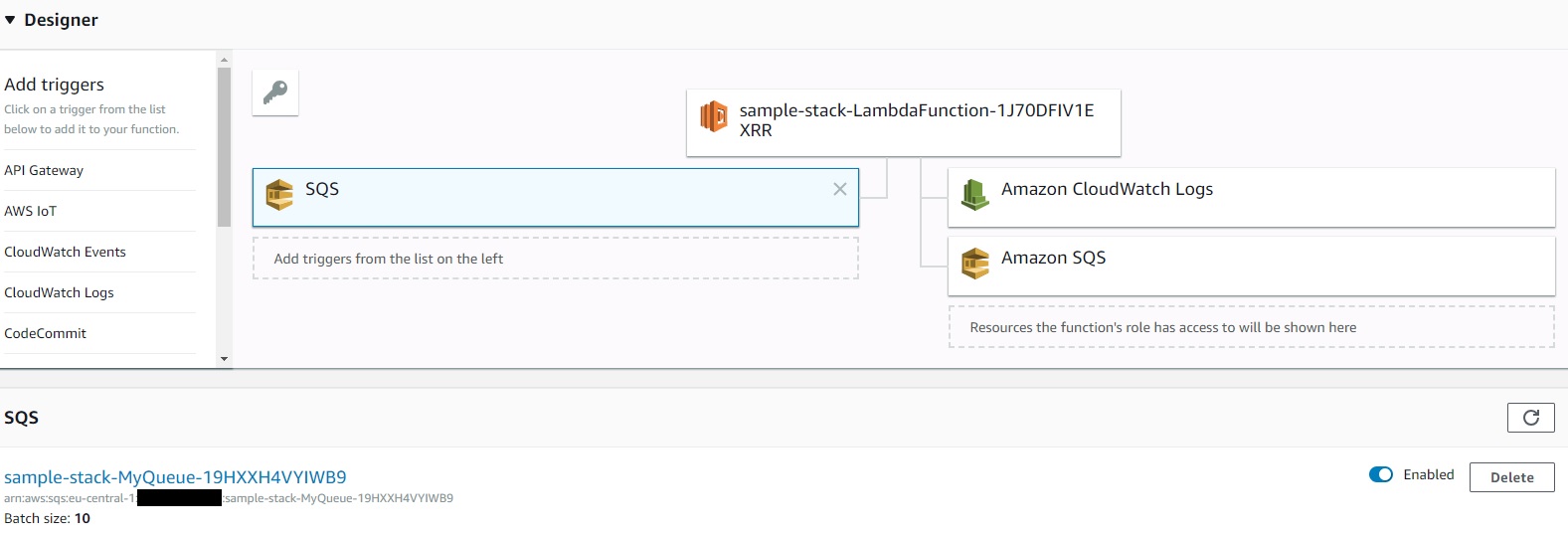
Since then I have seen many instructions explaining how to integrate this trigger via AWS Serverless Application Model (AWS SAM). Using this approach I noticed that when rolling out the SAM template via AWS CloudFormation a resource of type AWS::Lambda::EventSourceMapping is created. Since this resource is supported by AWS CloudFormation it should be possible to create the SQS Lambda trigger without SAM.
So I tried it successfully and got the following CloudFormation example template:
One thing to watch out for is that the lambda function timeout is not greater than the visible timeout on the queue. The solution can be tested by sending a test message via the SQS Queue using the SQS Console.
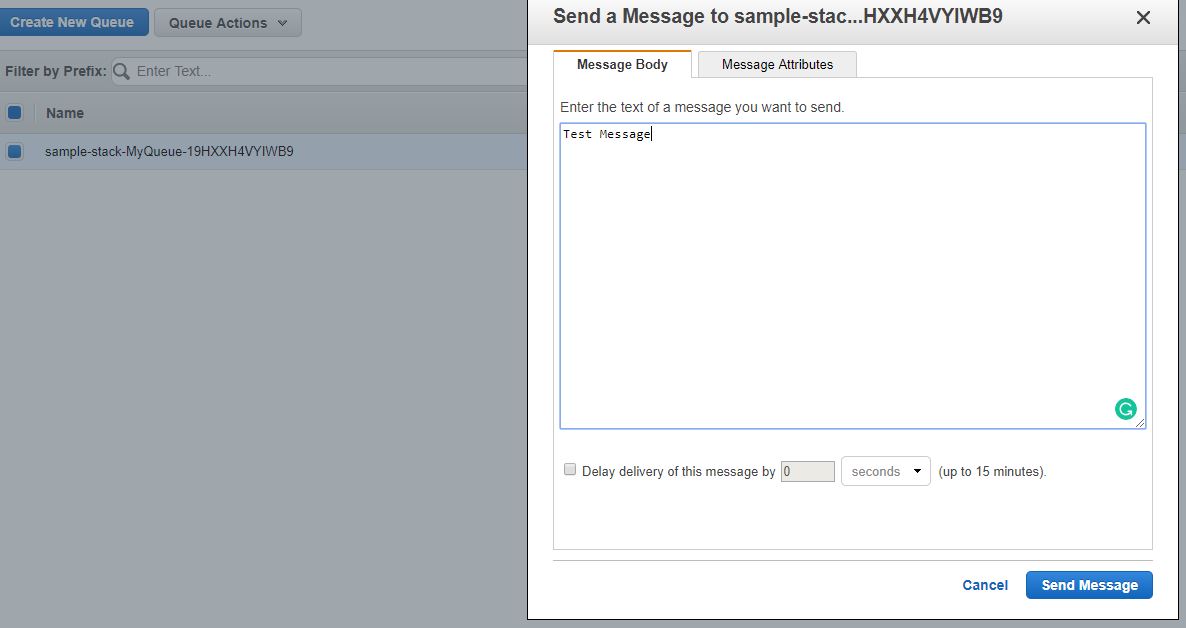 Sending a test message via the SQS Console
Sending a test message via the SQS Console
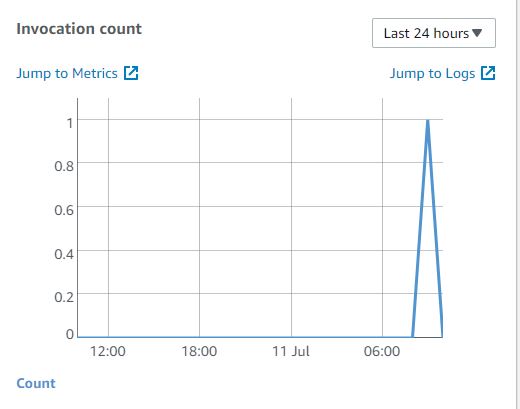 Check if the Lambda Function has been invoked
Check if the Lambda Function has been invoked
Read More
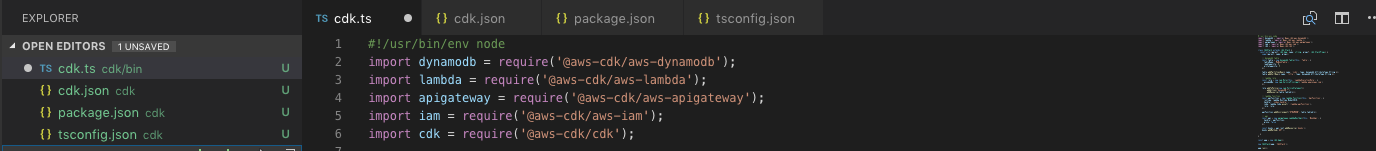 AWS has released a developer preview of AWS CDK during re:Invent 2018. A detailed description and the release informations can be found here:
AWS has released a developer preview of AWS CDK during re:Invent 2018. A detailed description and the release informations can be found here: 

 Sending a test message via the SQS Console
Sending a test message via the SQS Console Check if the Lambda Function has been invoked
Check if the Lambda Function has been invoked